The school library can manage a large number of books neatly and orderly. Accidentally stolen items can be quickly recovered. Our express delivery is always accurate on the route. Do you feel amazing? These are all based on RFID technology. In the Internet of Things era, it is one of the key technologies for data connectivity and communication.
What is RFID?
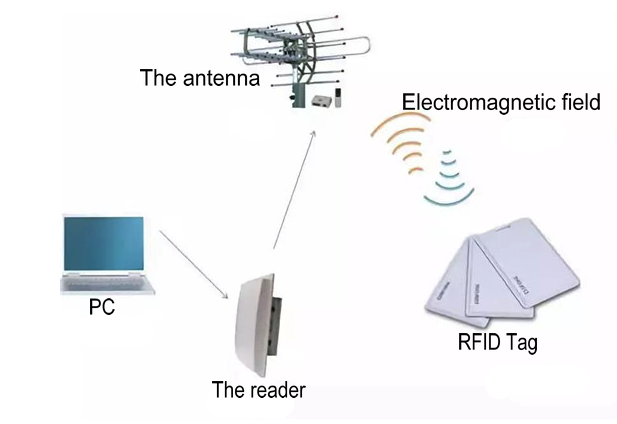
The full name of RFID is radio frequency identification. It is a wireless communication technology that can identify specific targets and read and write related data through radio signals. There is no need to establish mechanical or optical contact between the identification system and a specific target. Up to now, RFID has been widely used in all aspects of our lives.
- Tag: Each tag has a unique electronic code attached to the object to identify the target object.
- Reader: The device that reads label information can be designed as a handheld or fixed type.
- Antenna: It transmits radio frequency signals between tags and readers.
- Software: Software is necessary in any RFID system. Hardware cannot perform its basic functions without software.
The application of RFID technology has a half-world history. Today, RFID technology is developing well in the world.
Three categories of RFID products
Passive RFID product
Such products require touch to identify. Their main operating frequencies are low frequency at 125KHZ, high frequency at 13.56MHZ, ultra high frequency at 433MHZ and 915MHZ. The passive RFID product is quite common in our daily life. For example, both bus cards and ID cards are applications of passive RFID product.
Active RFID product
This type of product can be identified automatically over a long distance. Therefore, active RFID products are generally used in some large-scale environments. Their main operating frequencies are microwave 2.45GHZ and 5.8GHZ, UHF 433MHZ.
Semi-Active RFID Product
Semi-Active RFID Product is a combination of passive RFID product and active RFID product. That is to say, it combines the advantages of both. It can make microwave 2.45G play an advantage under the trigger of low-frequency 125KHZ frequency (short-range activation positioning, long-distance transmission of data), such as access control access management, regional positioning management, etc.
RFID technology has the characteristics of strong anti-interference and no manual identification. So, it is often used in some areas where information needs to be collected or tracked.
Six fields:
Warehouse Management and Cargo Transportation
Insert the RFID chip in every item. And then let the reader automatically collect the information about the goods. In this way, the managers can check the information about the goods at any time when the goods are stored in the warehouse or in the course of transportation.
Firstly, this will reduce the risk of discarding and stolen goods. Secondly, this will improve the speed and accuracy of delivery of goods. Further, this will prevent the channeling of goods.
Access Control and Attendance
In some companies or large conferences, people can identify and sign in by themselves through the identification system at the door. This makes things much easier.
Fixed Assets Management
Some places with huge assets and valuable items, such as libraries and museums, need complete management procedures and strict protection measures. When the stored information on these items changes abnormally, the administrator will receive this information immediately in the system.
Train and Car Identification and Baggage Safety Inspection
Railway vehicle dispatching system is a typical case. It can complete automatic identification of vehicle number and information input. Most importantly, it saves a lot of manual statistics time and improves accuracy.
Medical Information Tracking
Tracking cases, waste products, and drugs are good ways to improve the level and efficiency of hospital services.
Military and National Defense and National Security
Some important military drugs, guns, ammunition or military vehicles need to be tracked in real time.
Seven advantages:
Strong anti-interference
The reader can work in harsh environments. And it has strong penetration. Moreover, it can quickly identify and read labels.
Huge data capacity
The data capacity of the RFID tag can reach 10k, which is much higher than that of the 2,725 digits of the two-dimensional barcode.
Dynamically operable
When the object attached to the RFID tag enters the effective recognition range of the interpreter, the administrator can use programming to dynamically modify the tag’s data, and track and monitor it.
Long service life
It has strong anti-interference. In other words, it can work for a long time.
Conflict prevention
Within the effective recognition range of the reader, it can read multiple RFID tags at the same time.
High security
The RFID tag has high security. And we can encrypt tag data with a password to improve security.
Fast recognition
Generally, the recognition process does not exceed 100 milliseconds.
Top 10 Threats for RFID
1. Forgery
There are three types of RFID tags:
- Ordinary tags
- Symmetric key tags
- Asymmetric key tags
Ordinary tags are widely used in logistics management and tourism. However, ordinary tags are not encrypted and easy to forge. Therefore, the attackers can easily write information into a blank RFID tag or modify an existing tag to gain access to the authentication system.
In short, when the RFID tag contains sensitive information such as personal identity card, please be sure to encrypt the information.
2. Sniffing
Most RFID tags do not authenticate the reader’s legitimacy. So the attacker can use his own reader to send a request for authentication information to the tag and then grab the tag’s content.
3. Tracking
The attackers can use mobile robots to track the location of the tags. However, no matter whether the tag is encrypted or not, it can’t avoid being tracked.
4. Refusing
The readers and back-end databases are vulnerable to denial-of-service attacks. This will cause the reader to fail to authenticate the tags correctly and lead to the interruption of other corresponding services.
5. Deception
The attacker attempts to forge himself as an administrator of a back-end database. If the forgery succeeds, he can do anything.
6. Denial
When the denial occurs, the system has no way to verify whether the user has done this operation.
7. Insertion
In this attack, the attacker inserts a system command into the normal data stored in the tag.
8. Retransmission
The attacker intercepts the communication between the tag and the reader. Then he records the reader’s response to the tag’s authentication request. After that, he retransmits the information to the reader.
9. Physical attack
The attackers can use X-rays to destroy tag content. Similarly, they can also use electromagnetic interference tags to communicate with readers. In addition, anyone can easily use a knife or other tools to destroy labels.
10. Virus
RFID system is vulnerable to virus attack. In most cases, the target of the virus is the back-end database. RFID virus can destroy and leak the tag content stored in the back-end database. Moreover, it can reject or interfere with the communication between the reader and the back-end database.
Developing Trend
In recent years, the application of the Internet of Things technology has developed rapidly. Therefore, as one of the main technologies of the Internet of Things, RFID has attracted more and more attention.
So, what role should EAS play in this era? Will it disappear? Or keep pace with the times? Certainly, as an effective anti-theft technology, EAS will not end its historical mission.
In the long run, the integration of EAS and RFID technology is a general trend. The current EAS tag can not store goods information. But, RFID tag information capacity is large, and the information can be modified. Therefore, the anti-theft information and goods information can be written into the RFID tag.
In the future, the combination of EAS and RFID will be more and more widely used to protect goods and manage inventory.
